As many expected, the most significant financial scam on the internet comes from a threat known as “Business Email Compromise” (BEC) . Last year BEC losses from businesses were over $2.4 billion dollars, with nearly 20,000 unique complaints sent to the FBI about these types of attacks.
The FBI described BEC risks and the context for some of these attacks in their report, writing:
“BEC/EAC is a sophisticated scam targeting both businesses and individuals performing transfers of funds. The scam is frequently carried out when a subject compromises legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
As fraudsters have become more sophisticated and preventative measures have been put in place, the BEC/EAC scheme has continually evolved in kind. The scheme has evolved from simple hacking or spoofing of business and personal email accounts and a request to send wire payments to fraudulent bank accounts.
These schemes historically involved compromised vendor emails, requests for W-2 information, targeting of the real estate sector, and fraudulent requests for large amounts of gift cards.”
As businesses continue to encourage and increase remote meetings due to the COVID pandemic, the report pointed out that they are at even greater risk of more novel BEC attack strategies:
“Now, fraudsters are using virtual meeting platforms to hack emails and spoof business leaders’ credentials to initiate the fraudulent wire transfers. These fraudulent wire transfers are often immediately transferred to cryptocurrency wallets and quickly dispersed, making recovery efforts more difficult. The COVID-19 pandemic and the restrictions on in-person meetings led to increases in telework or virtual communication practices. These work and communication practices continued into 2021, and the IC3 has observed an emergence of newer BEC/EAC schemes that exploit this reliance on virtual meetings to instruct victims to send fraudulent wire transfers.
They do so by compromising an employer or financial director’s email, such as a CEO or CFO, which would then be used to request employees to participate in virtual meeting platforms. In those meetings, the fraudster would insert a still picture of the CEO with no audio, or a ‘deep fake’ audio through which fraudsters, acting as business executives, would then claim their audio/video was not working properly. The fraudsters would then use the virtual meeting platforms to directly instruct employees to initiate wire transfers or use the executives’ compromised email to provide wiring instructions.”
Dangling Domains: An often overlooked threat exposing companies to BEC risks
At the Me2B Alliance, we know that the threats from Business Email Compromises are complex and require an “all hands on deck” approach in order to keep people safe.
Our team has focused on the particular data supply chain risk resulting in Business Email Compromises wherein a business or organization forgets to renew one of their internet domains (resulting in a “dangling domain”). Scammers then swoop in and renew the domain in order to conduct scams or exploits against users. Our team has not yet documented any specific BEC attacks yet, in our nascent efforts of identifying and reporting “dangling domains”.
“Organizations that forget to renew ALL their registered domains are vulnerable to serious attacks. We believe more work needs to be done by the private and public sectors to address these vulnerabilities. We hope our ongoing efforts to highlight dangling domain risks help policymakers and the public better understand the implications”. – Lisa LeVasseur, Executive Director, Me2B Alliance
Last October, we uncovered a popular SDK called “Asking Point” which has been installed in over 150 iOS/Apple mobile apps. The SDK parent company had gone out of business and yet their domain embedded into these apps was for sale for just over $3,500. This left the window wide open for someone to purchase this domain and pose as the parent company – leaving users vulnerable to BEC scams. In an effort to close this “loophole”, our team reached out to Apple alerting them of the threat and ultimately resulting in them acquiring the domain to keep it from landing in the hands of scammers or criminals.
In December, our team released Spotlight Report #4, a deeper look at data supply in K12 school utility apps. During the course of our research, we discovered three school-related dangling domains (used by three separate public schools). All three domains have ongoing Business Email Compromise risks, leaving students and parents vulnerable to attack. We shared our findings with the FTC, but as yet have seen no indication that any government agency has warned these three schools districts domains or domains similar to them:
Dangling domains leave school systems and students vulnerable to scams
- Santa Monica-Malibu USD Android App from Blackboard Inc.: The Santa Monica-Malibu high school’s android app had the dangling domain “Malibuhigh.org”. This domain currently hosts a fake legal website, posing risks from Business Email Compromise schemes or other phishing exploits.
- Maryland’s largest school district’s Android App, also from Blackboard Inc.: Magruder High School in Maryland had already lost their sports domain by the time we figured it out, with Magruderathletics (WARNING).org being compromised and still hosting malicious redirects to this very day. After the Me2B Alliance alerted Blackboard Inc., they were able to quickly remove removed this domain from their active mobile app, reducing some of the risks. This is also an active domain, and Business Email Compromise risks for emails that originate from this domain (i.e. “@Magxxxxathletics.org”) remains a real threat.
- Quinlan, Texas School District : Quinlan, TX school district had a domain that went up for sale for $30 that was integrated into their Android app. The domain was purchased before anyone could take action. After the Me2B Alliance alerted Blackboard Inc., the dangling domain link was removed from the app, and subsequently the Android app was pulled down from the Google Play Store.
The importance of discovering and remediating Dangling Domains
Your domains are valuable assets and play an integral part in both the day-to-day operations of your business and the trust you build with all stakeholders. If you discover you have lost a domain that is associated with your organization, we advise treating this as a potential security breach. A dangling domain leaves you vulnerable to scammers masquerading as your organization. You should alert all vendors and internal staff that that this domain is no longer trustworthy and advise them to no longer consider communication from this domain legitimate.
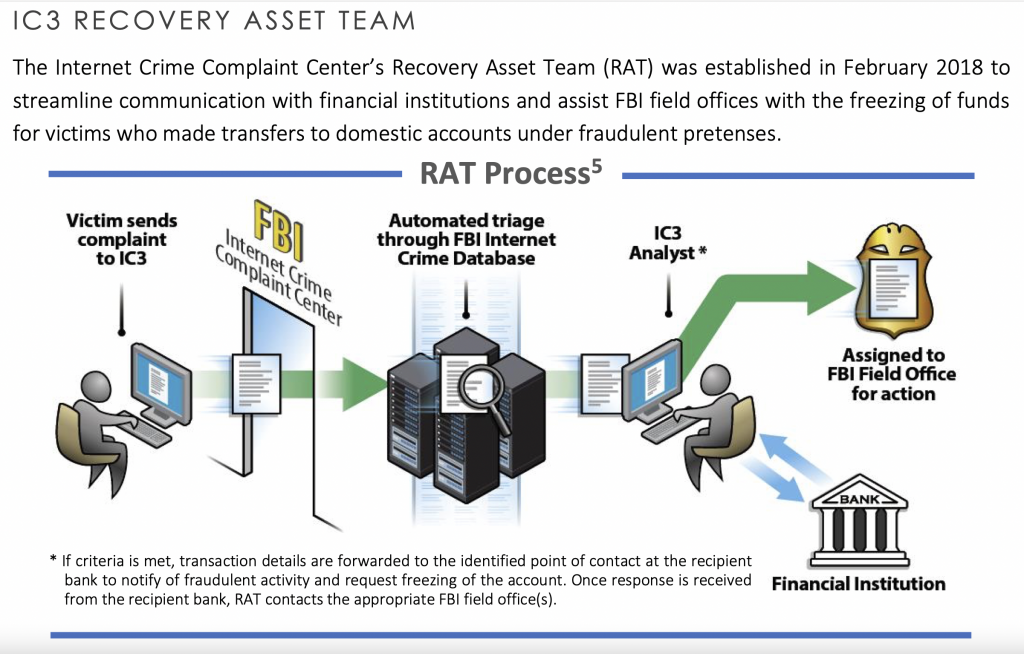
The FBI encourages you to contact your bank as quickly as possible, if your organization has been a victim of BEC or a hijacked domain. The FBI also encourages you to reach out directly to your local FBI office, and/or report the crime to the FBI’s Internet Crime Complaint Center (IC3). Taking action as quickly as possible improves your chance of reducing financial ramifications.
This infographic outlines the process the FBI uses for these types of public risks, as described in their recent report:
Me2BA continues to monitor and discover Dangling Domains
The US Federal Chief Information Security Officer Council (CISO Council) has confirmed that they do not monitor for dangling domains outside of the .gov top level domain. In light of that, Me2BA has recently developed an automated tool to search for dangling domains related to education, civic, and safety URLs. We’ve already sent our first responsible disclosures to some organizations whose domains are currently for sale. We will continue to share our findings here. Note that to do this job properly requires significantly more resources, and we look forward to partnering with other like-minded businesses to develop a more robust solution
We are here to help
Are you aware of any dangling domains or concerned about risks from this within any specific apps? Reach out to our team at contact@internetsafetylabs.org.
