Version 1.0 | September 1, 2021
#InvisibleParallelDataverse #RespectfulTech #DystopianMetaverse
IN A NUTSHELL
The reality of online data flows is nothing like what we expect. Our personal data flows do not start light and increase with time and trust. Instead, a firehose of personal information is released – and shared with a host of unseen third parties – as soon as we open an app or website. Me2BA’s Respectful Tech Specification V.1 is largely focused on testing for these invisible parallel dataverse data flows.
So far in this series of Me2B 101 Flash Guides, we’ve focused on the digital world as we interact with and experience it. We now turn our attention to the flow of data during the Me2B Relationship lifecycle.
Figure 10.1 illustrates typical user expectations about data sharing over the course of the Me2B Lifecycle. It reflects our expectations – based on the relationship norms in the physical world – that the flow of personal information would start off very slowly, only to build up over time as our trust builds.
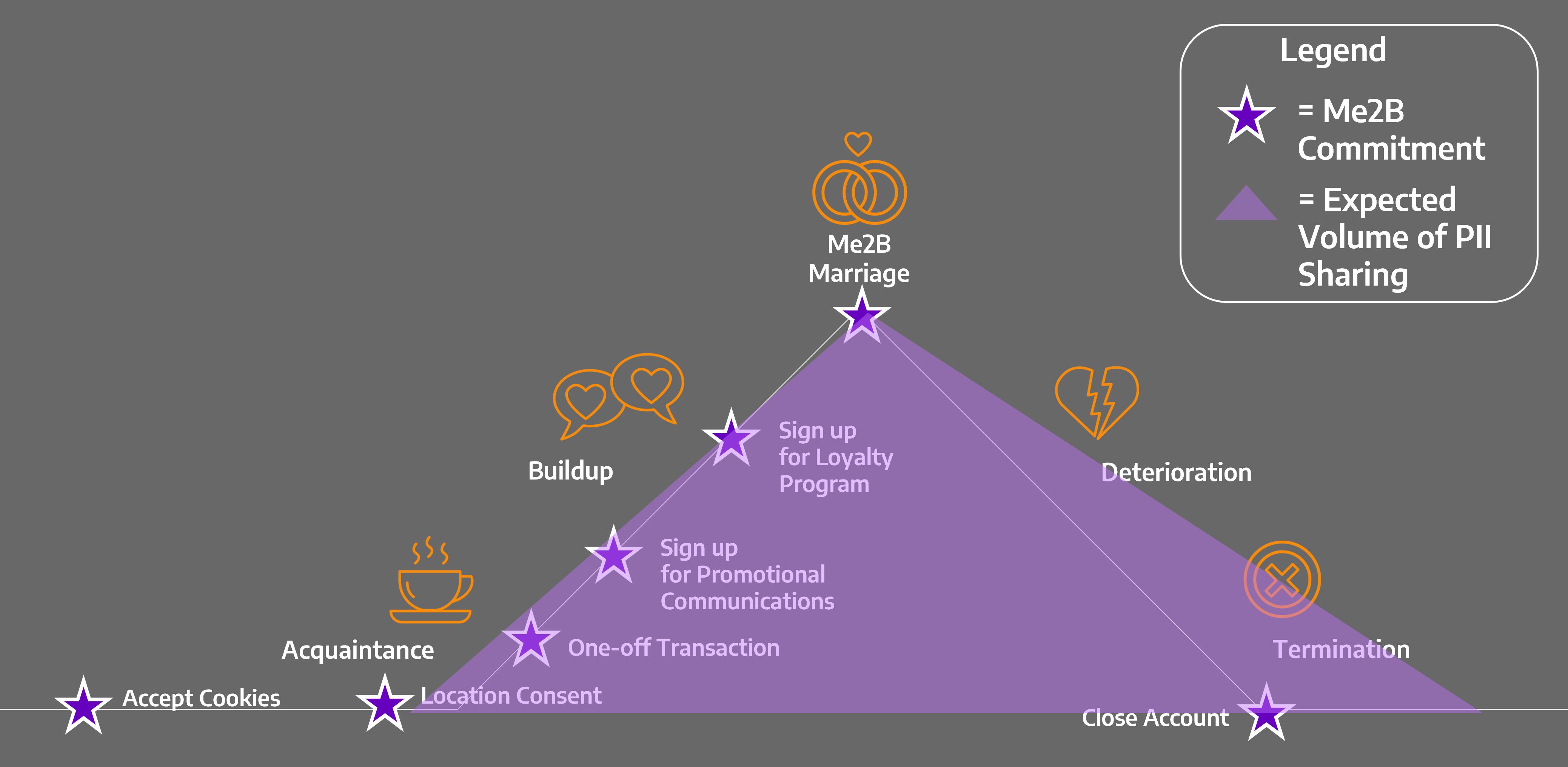
Figure 10.1
This is the [somewhat] idealized view of how our digital Me2B Relationships should be – reflecting the increasing trust between the Me and the B over time, and a proportional increase in information sharing over time. It would be more ideal if the flow of information ceased more cleanly at the end of a Me2B Marriage, but that doesn’t appear to be the case for most services.
Moreover, this idealized lifecycle is not at all the current reality of digital Me2B Relationships.
Instead, as soon as we so much open a website or an app, there is a firehose of information about us being shared with countless undisclosed entities—Data Processors (or Hidden B2B Affiliates, as introduced in Flash Guide #6).I The reality looks more like Figure 10.2 than 10.1.
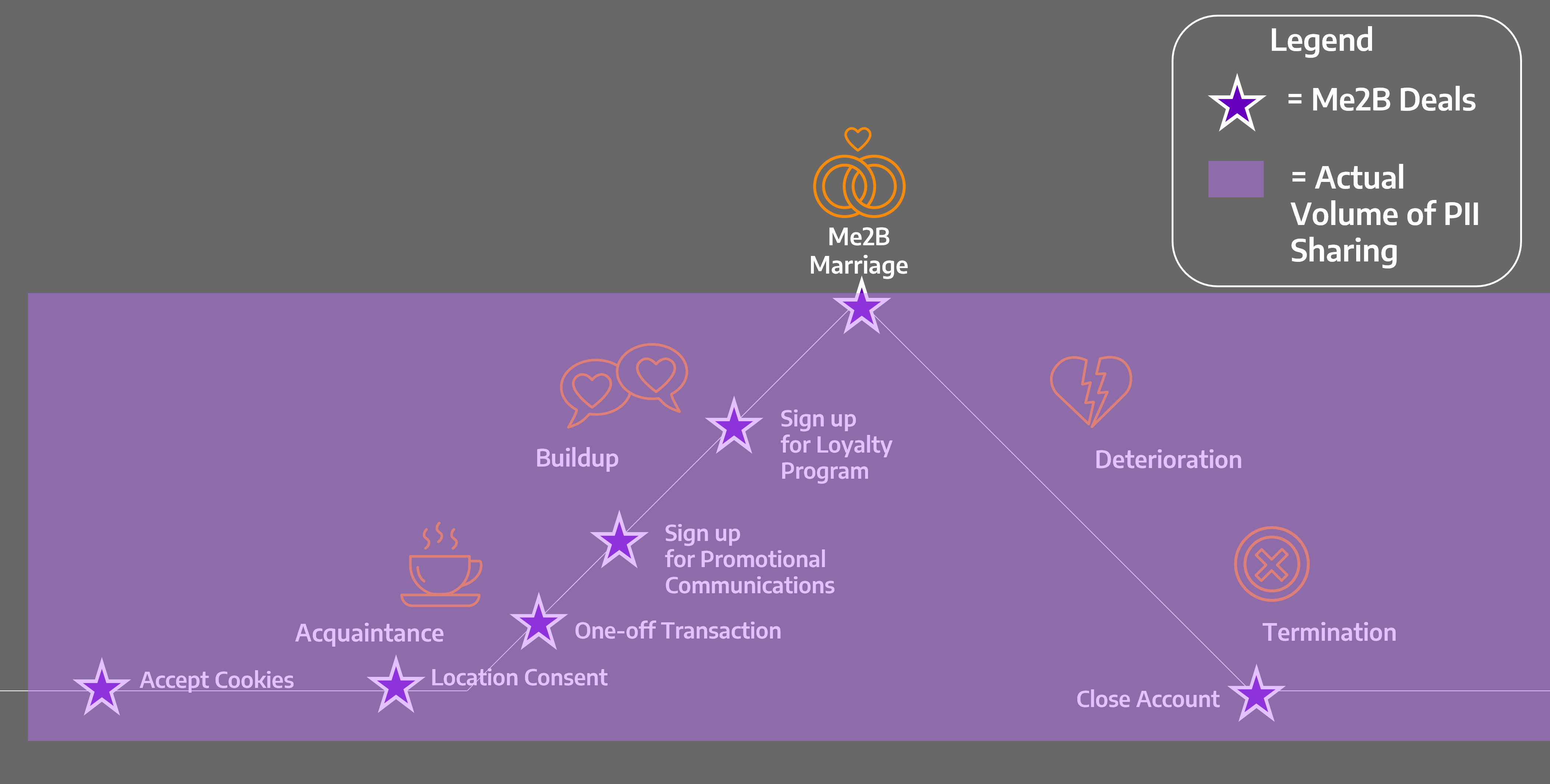
Figure 10.2 Invisible Parallel Dataverse
How Does This Happen?
A major culprit in the tsunami of unwitting information sharing is the digital advertising infrastructure, (described in Flash Guide # 5) which systematically, and at massive scale shares personal data with multiple third parties (aka Data Processors). So long as this infrastructure exists, the personal data floodgates are open.ii
Digital advertising is just one of the ways that websites and apps invisibly share data with third party Data Processors. Until all these avenues are exposed, and businesses and other Data Controllers are made responsible for respectful data processing, people are at risk. Version 1.0 of the Me2B Respectful Tech Spec is largely dedicated to testing for [outbound] invisible parallel dataverse data flows.
- See Flash Guide 6 for how GDPR terms such as “Data Processor” and “Data Controller” map onto Me2B Alliance terminology.
- See our July 4, 2021 blog post on Freedom in the Digital World https://internetsafetylabs.org/blog/insights/freedom-in-the-digital-world/
© Me2B Alliance 2021
